

![]()
The Data Encryption Standard (DES) is the most well-known symmetric-key block cipher. Recognized world-wide, it set a precedent in the mid 1970s as the first commercial-grade modern algorithm with openly and fully specified implementation details. It is defined by the American standard FIPS 46-2.
The DES algorithm uses a 56-bit encryption key, meaning that there are 72,057,594,037,927,936 possible keys. The DES Key Search Project developed specially designed hardware and software to search 90 billion keys per second.
A key consists of 64 binary digits ("0"s or "1"s) of which 56 bits are randomly generated and used directly by the algorithm. The other 8 bits, which are not used by the algorithm, are used for error detection. The 8 error detecting bits are set to make the parity of each 8-bit byte of the key odd, i.e., there is an odd number of "1"s in each 8-bit byte. Authorized users of encrypted computer data must have the key that was used to encipher the data in order to decrypt it. The encryption algorithm specified in this standard is commonly known among those using the standard. The unique key chosen for use in a particular application makes the results of encrypting data using the algorithm unique. Selection of a different key causes the cipher that is produced for any given set of inputs to be different. The cryptographic security of the data depends on the security provided for the key used to encipher and decipher the data.
Algorithm:
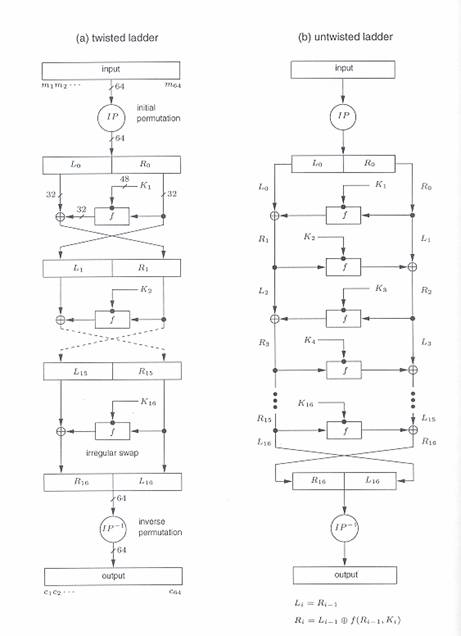
INPUT: plaintext m1 … m64; 64-bit key K = k1 … k64 (includes 8 parity bits).
OUTPUT: 64-bit cipher text block C = c1… c64.
IP
58 50 42 34 26 18 10 2
60 52 44 36 28 20 12 4
62 54 46 38 30 22 14 6
64 56 48 40 32 24 16 8
57 49 41 33 25 17 9 1
59 51 43 35 27 19 11 3
61 53 45 37 29 21 13 5
63 55 47 39 31 23 15 7
IP-1
40 8 48 16 56 24 64 32
39 7 47 15 55 23 63 31
38 6 46 14 54 22 62 30
37 5 45 13 53 21 61 29
36 4 44 12 52 20 60 28
35 3 43 11 51 19 59 27
34 2 42 10 50 18 58 26
33 1 41 9 49 17 57 25
E
32 1 2 3 4 5
4 5 6 7 8 9
8 9 10 11 12 13
12 13 14 15 16 17
16 17 18 19 20 21
20 21 22 23 24 25
24 25 26 27 28 29
28 29 30 31 32 1
P
16 7 20 21
29 12 28 17
1 15 23 26
5 18 31 10
2 8 24 14
32 27 3 9
19 13 30 6
22 11 4 25
Even today, when DES is no longer considered a practical solution, it is often used to describe new cryptanalytical techniques. It is remarkable that even today, there are no cryptanalytical techniques that would completely break DES in a structural way, indeed, the only real weakness known is the short key size (and perhaps the small block size).
Original Text:
Se necesitan dos años para aprender a hablar y sesenta para aprender a callar. Una frase de un personaje complejo que vivió intensamente y que escribió hasta lo que debió callar.
Encrypted Text with phrase: securenet2002:
B97E86C541D45DAC45DA7DEE6DBF57A374E13146DB2A3E9CCD70E377BD4DCA42D554DC3B69
FA2BA170B747DD2227CE8B8ADD61F657B87FFC180B181752C70A4C81DD31F30550C386878D8D
CB1DBFDF73F62FE8383DCD25F2548999CF46031BFC6FBA4EA56DEE6DFE5BB3B6799D798C969
E7DDECE70D74E0BE239DD2278FD13B3184D898F9560B06D8487C2485AFB4194C748D849C956D
6256DBF18498E70B4B751B2B747D94B598DC217F382C150C355AF7492F2